今晚在折腾集群管理问题,其中最重要的一个问题就是需要各节点的免密码登录,那就必须在各个机器上配置公钥。
配置公钥
ssh-keygen
将公钥复制到被控制机器中,实现免密码登录
ssh-copy-id -i ~/.ssh/id_rsa.pub -p 22 root@目标ip
正常情况下执行这两步就已经可以了,但是我遇到了一个问题,就是有的机器没有问题,可以正常直接登录,但部分机器,永远都是公钥通不过,需要密码登录。
无法公钥登录的解决
登陆时执行如下命令查看详细日志
ssh x.x.x.x -vvv
debug1: Unspecified GSS failure. Minor code may provide more information
No Kerberos credentials available (default cache: KEYRING:persistent:0)
debug1: Unspecified GSS failure. Minor code may provide more information
No Kerberos credentials available (default cache: KEYRING:persistent:0)
debug2: we did not send a packet, disable method
debug3: authmethod_lookup publickey
debug3: remaining preferred: keyboard-interactive,password
debug3: authmethod_is_enabled publickey
debug1: Next authentication method: publickey
debug1: Offering RSA public key: /root/.ssh/id_rsa
debug3: send_pubkey_test
debug2: we sent a publickey packet, wait for reply
debug1: Authentications that can continue: publickey,gssapi-keyex,gssapi-with-mic,password
debug1: Trying private key: /root/.ssh/id_dsa
debug3: no such identity: /root/.ssh/id_dsa: No such file or directory
debug1: Trying private key: /root/.ssh/id_ecdsa
debug3: no such identity: /root/.ssh/id_ecdsa: No such file or directory
debug1: Trying private key: /root/.ssh/id_ed25519
debug3: no such identity: /root/.ssh/id_ed25519: No such file or directory
debug2: we did not send a packet, disable method
debug3: authmethod_lookup password
debug3: remaining preferred: ,password
debug3: authmethod_is_enabled password
debug1: Next authentication method: password
这里大家对比下正常登录的日志是可以看到区别的,但是也看不出问题所在。
网上找了几个小时的资料,试了各种方法,比如:
- sshd_config配置
HostKey /etc/ssh/ssh_host_rsa_key RSAAuthentication yes PubkeyAuthentication yes AuthorizedKeysFile .ssh/authorized_keys
- selinux配置
- 目录及文件权限调整
- 文件格式问题
几乎所有问题都排查了,仍然不行,但是在查看日志: /var/log/secure 还是可以看出端倪
Feb 8 00:01:42 izwz90g1ws14xwy7e4fqe3z sshd[7454]: Authentication refused: bad ownership or modes for directory /root
Feb 8 00:35:48 izwz90g1ws14xwy7e4fqe3z sshd[15171]: Authentication refused: bad ownership or modes for directory /root
Feb 8 00:38:22 izwz90g1ws14xwy7e4fqe3z sshd[18337]: Authentication refused: bad ownership or modes for file /root/.ssh/authorized_keys
Feb 8 00:38:39 izwz90g1ws14xwy7e4fqe3z sshd[18337]: Connection closed by 120.77.212.168 [preauth]
Feb 8 00:38:41 izwz90g1ws14xwy7e4fqe3z sshd[18742]: Authentication refused: bad ownership or modes for directory /root 其实这里相关的资料网上也找了不少,也都各种尝试给权限:
chmod g-w /home/your_user # 或 chmod 0755 /home/your_user
chmod 700 /home/your_user/.ssh(~/.ssh)
chmod 600 /home/your_user/.ssh/authorized_keys(~/.ssh/authorized_keys)
但是发现并没有什么用,确认了.ssh 目录 和 authorized_keys文件的权限都没有问题,仍然不奏效。
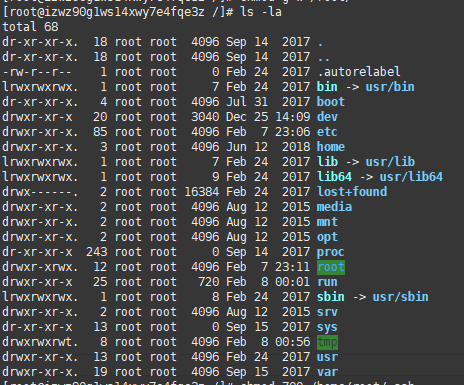
因为我是root用户家目录就是/root,突发奇想看看/root根目录的权限,发现是737,而正常可以连接的机器/root权限没这么高,是550
无法登陆的机器:
正常机器:
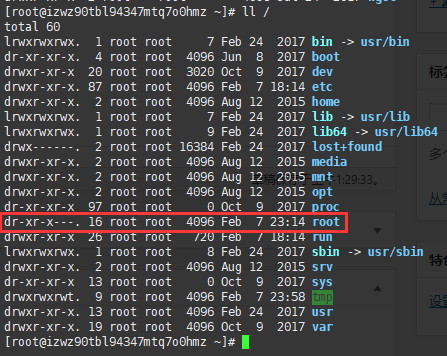
所以 chmod 550 /root 解决该问题。
总结
其实这个问题的出现很简单,由于平时发现各种权限不足,就chmod -R 777 怼上去,总觉得这么怼不好,今天终于体会到除了安全问题之外的其他困扰。
因为ssh 对权限限制比较严,所以对于私钥和公钥文件的目录及文件权限要求比较严,低了不行,高了也不行,所以容易出现这种情况。
另外也可以在ssh_config 文件里加上配置:StrictModes off 解决这个问题,但是不建议走这种捷径,解决权限问题为主。
![扫一扫本文二维码,分享给大家 SSH 配置公钥登录无效仍需输入密码[一个微妙的问题点]](https://www.vuln.cn/wp-content/themes/wpgo/caches/461f1a8f4ce8fcafbce2e98bb07468c3.jpg)




![Connectify Dispatch指定程序使用指定网卡[运维神器]](http://www.vuln.cn/wp-content/uploads/2016/11/1.jpg)
![网站备案流程_网站备案需要什么[简单明了解决备案各种问题]](http://www.vuln.cn/wp-content/uploads/2014/03/topleft.gif)
![最新BurpSuite 1.7.32 破解版[注册机]下载【无后门版】](http://www.vuln.cn/wp-content/uploads/2018/02/ee462f76d3e2440f67041f92499c36ae.png)
![php一句话后门的几种变形分析[preg_replace函数]](http://www.vuln.cn/wp-content/uploads/2016/11/11.jpg)



![[网盘下载] GB/T 23031. 1 — 2022 工业互联网平台 应用实施指南 第一部分:总则.pdf](http://www.vuln.cn/wp-content/uploads/2023/02/3faee12ec28ab59793fbe1c203b8363f.png)
![[网盘下载] GB/T 41870-2022 工业互联网平台 企业应用水平与绩效评价.pdf](http://www.vuln.cn/wp-content/uploads/2023/02/4ec246e126c4f3a41d9ced588c790998.png)
![[网盘下载] GB/T 36323-2018 信息安全技术 工业控制系统安全管理基本要求.pdf](http://www.vuln.cn/wp-content/uploads/2023/02/f6adb0f6fa49a734846c5873d178bfbc.png)
![[网盘下载] GB/T 32919 -2016 信息安全技术 工业控制系统安全控制应用指南.pdf](http://www.vuln.cn/wp-content/uploads/2023/02/da9420e72b7af6bfb4fa273884dcefc1.png)

 云悉指纹
云悉指纹